Get an applicable workaround to get rid of Ads by Dragon Branch, which implies eradicating the respective adware add-on from affected web browsers.
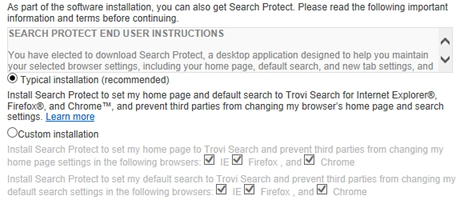
Dragon Branch is a malicious browser extension which exhibits extraordinary persistence and distorts the look and feel of websites visited on the PC that got infected. Just like in any average adware attack context, the add-on is marketed as something helpful and safe – it even has a site that describes the purported benefits of using it in a nutshell. The good part about this app doesn’t go any further than words, though, because its genuine objective has nothing to do with improving one’s Internet searching activities. The fact of the matter is that Dragon Branch pursues nothing but intrusive advertising goals and deploys this at the expense of the victim’s peace of mind and browsing experience.
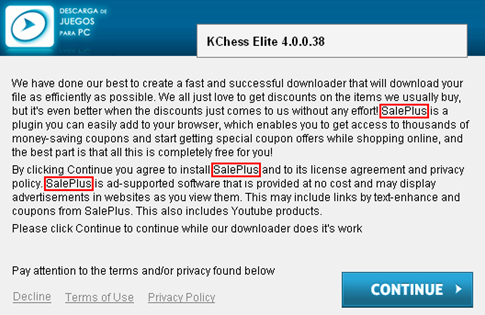
Even a quick glance at the application’s web page is enough to realize that it, obviously, does not provide the download option. The reasoning behind such a weird state of things is that the adware developers are using other channels to distribute their adverse product. Compromised users have reportedly caught this bug when installing free software off of questionable sites and in some cases even on web resources with immaculate reputation. The virus is built into the setup for multiple open-source tools, including cracked Adobe Flash Player updates, media players, streaming video downloaders and similar potentially popular utilities. In most cases the users opt into the bundle without noticing it.

Misguiding description of Dragon Branch on its site
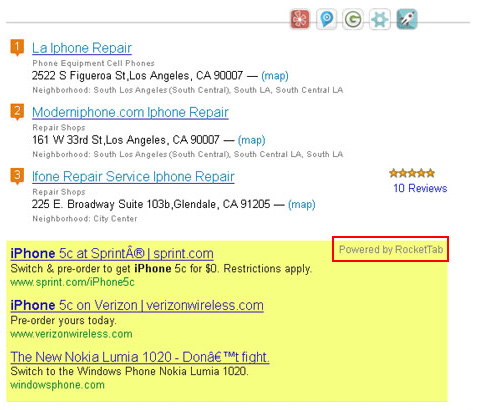
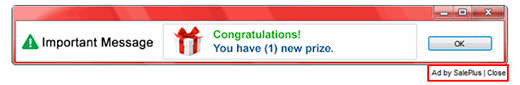
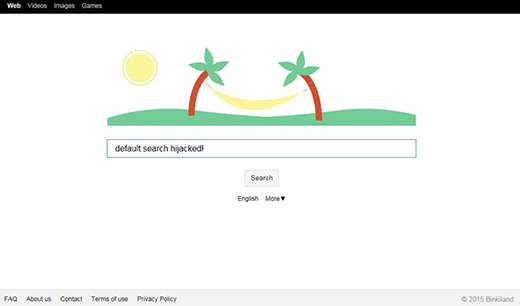
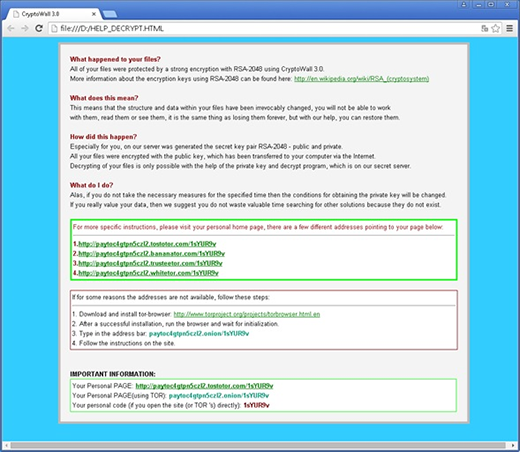
Dragon Branch adware operates on the infected computer as an add-on which appears on the extensions list for Firefox, Chrome and IE without being authorized by the PC admin. The add-on also modifies the system registry entry for Internet Explorer under HKEY_CURRENT_USER, in particular the start page value which gets configured to point to an adult site. The symptom that drives people nuts after all of these unwarranted changes take effect is the injection of sponsored entities into web pages. These objects are signed “Dragon Branch Ads”, mainly containing X-rated images and recommending the victim to click and be redirected to shady sites. The ads are displayed over the original text and graphics on pages and in most cases cannot be closed without browser diverting taking place.
The outcomes of Dragon Branch’s activity are both embarrassing and irritating, but the affected users are at their wit’s end when trying to fix it. Some of the removal hurdles occur because not all antiviruses detect this adware. Furthermore, if you try to uninstall this app manually, it reappears shortly or gets replaced by other viruses such as Buzzdock and Conduit. In order to bypass the above-mentioned persistence of Dragon Branch, it’s recommended to use the adware-specific removal instructions covered below. Just follow the steps and make your system virus-free.
Automatic removal of the Dragon Branch virus
When it comes to handling infections like this one, using a reputable cleaning tool is the place to start. Sticking to this workflow ensures that every component of the adware gets found and eradicated from the affected computer.
1. Download and install the cleaning tool and click the Start Computer Scan button
Download Dragon Branch Ads removal tool
2. The wait is worth it. Once the scan completes, you will see a report listing all malicious or potentially unwanted objects detected on your PC. Go ahead and click the Fix Threats option in order to get Dragon Branch automatically uninstalled from your machine. This being done, you should be good to go. Just to make sure everything went smooth, consider going through the steps below real quick.
Uninstall troublesome program through Control Panel
- From your Windows menu, go to Control Panel. Select Add or Remove Programs (for Windows XP / Windows 8) or Uninstall a program (Windows Vista / Windows 7)
![Uninstall a program]()
- Look carefully through the list and locate Dragon Branch. Select the bug and click Uninstall
![Uninstall Dragon Branch]()
Remove Dragon Branch Ads virus from web browsers manually
The workflow covered below is intended to undo all changes that the Dragon Branch infection made to Chrome, Firefox and Internet Explorer. Be advised there’s some collateral inconvenience you will encounter, namely the loss of all installed add-ons and personalized information (saved passwords, cached data, bookmarks and other content).
Reset Chrome
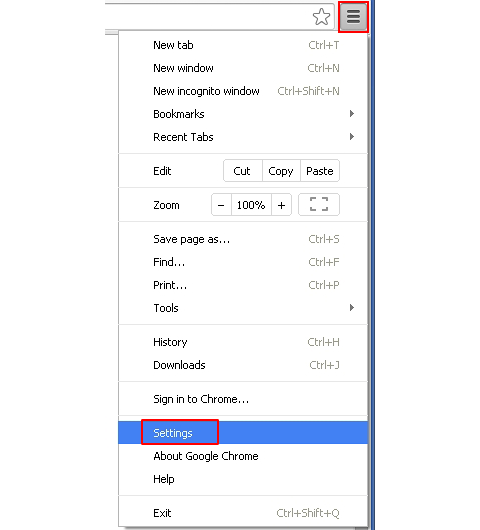
- Open Google Chrome. Click the Chrome menu icon as shown on the image and select Settings
![Reset Chrome 1]()
- Click Show advanced settings
![Reset Chrome 2]()
- Hit the Reset browser settings button
![Reset Chrome 3]()
- On the warning that popped up, read everything you should know about the consequences of the reset. Click Reset if you want to complete the procedure
![Reset Chrome 4]()
- Restart Chrome for the changes to take effect
Reset Firefox
- Open Firefox. Go to Help > Troubleshooting Information or type about:support in the URL field
![Reset Firefox 1]()
- Click Reset Firefox button to get the job done
![Reset Firefox 2]()
- Restart Firefox for the changes to take effect
Reset Internet Explorer
- Open IE. Go to Tools > Internet Options
![Reset Internet Explorer 1]()
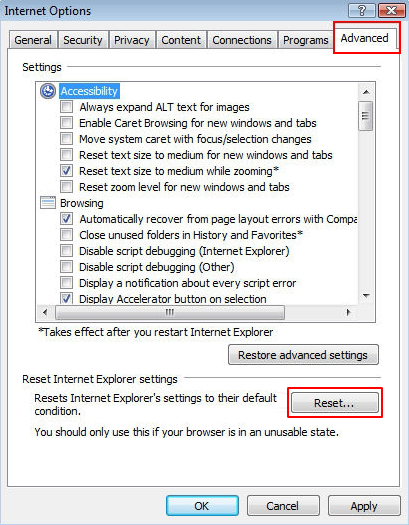
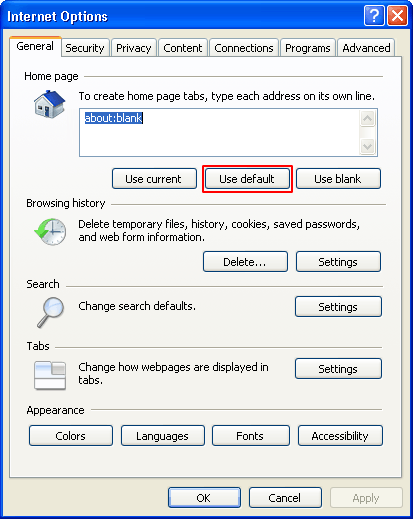
- Hit the Advanced tab and click Reset
![Reset Internet Explorer 2]()
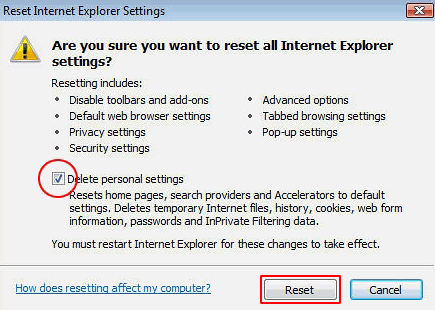
- Make sure the Delete personal settings option on the Reset Internet Explorer Settings dialog is ticked and click Reset
![Reset Internet Explorer 3]()
- Restart Internet Explorer for the changes to take effect
Did the problem go away? Check and see
Computer threats like Dragon Branch can be stealthier than you can imagine, skillfully obfuscating their components inside a compromised computer to evade removal. Therefore by running an additional security scan you will dot the i’s and cross the t’s in terms of the cleanup.
Download Dragon Branch scanner and remover
The post Remove Dragon Branch Ads virus from Chrome, Firefox and IE appeared first on Keone Software.