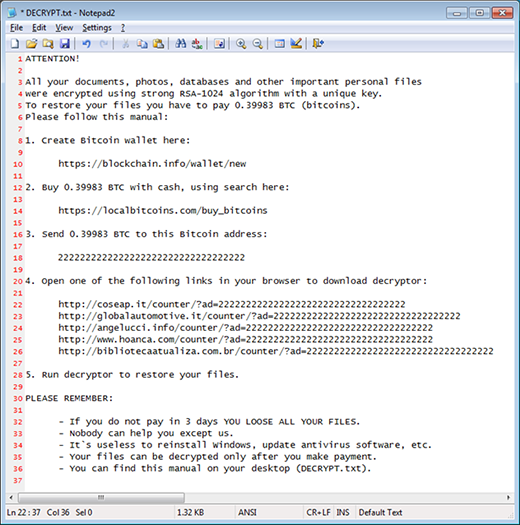
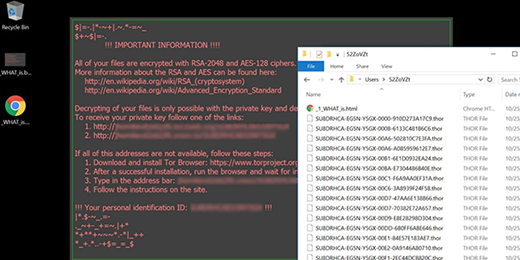
The post describes and advises on handling a ransomware variant that adds .crypt to filenames and creates de_crypt_readme ransom payment instructions.
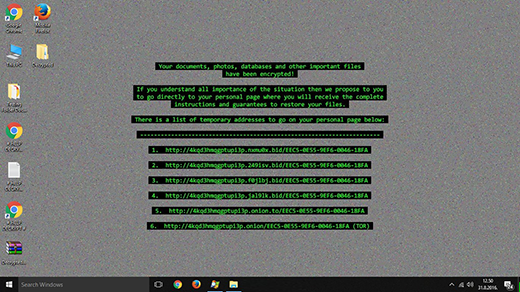
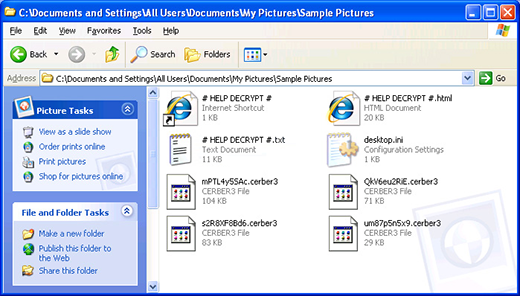
It’s startling what ideas can occur to cybercriminals with plenty of tech expertise and time on their hands. File encrypting ransomware is probably these ill-minded individuals’ worst-ever invention, given the consequences for the computer users who fall victim to these types of attacks. One’s personal files can no longer be accessed, and there is a pending demand of a ransom to recover the information. One of the recent samples is trying to impersonate other widespread crypto viruses as far as the look and feel are concerned, but it turned out to have been devised independently. The strain in question encrypts data with the RSA4096 algo, appends files with the .crypt component, and drops three editions of ransom notes: de_crypt_readme.html, de_crypt_readme.bmp, and de_crypt_readme.txt.
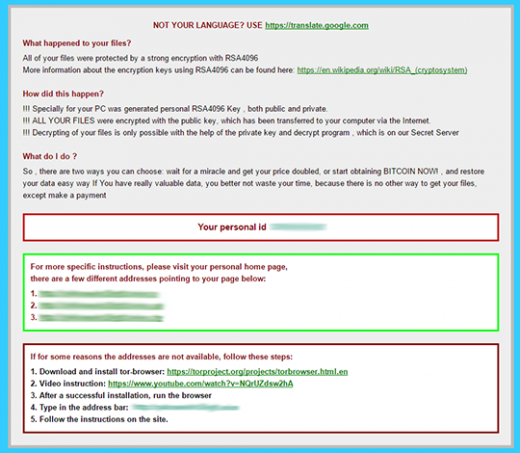
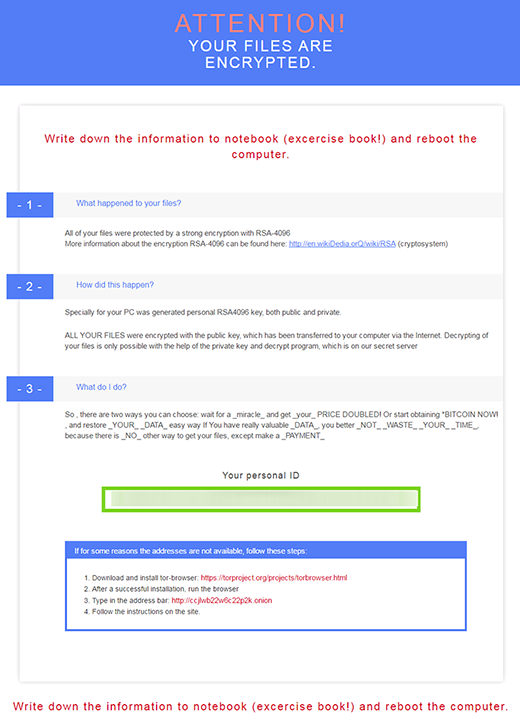
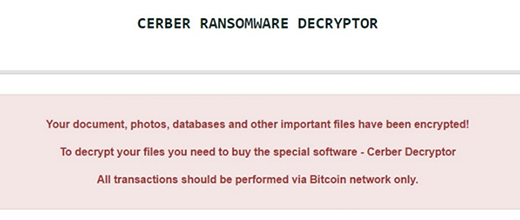
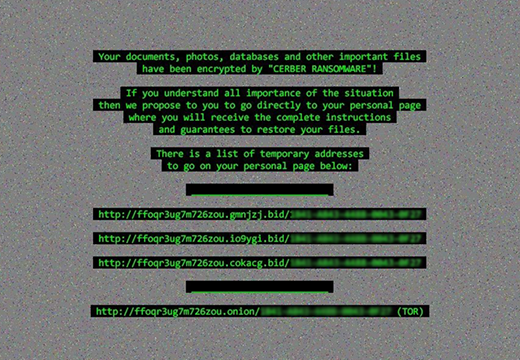
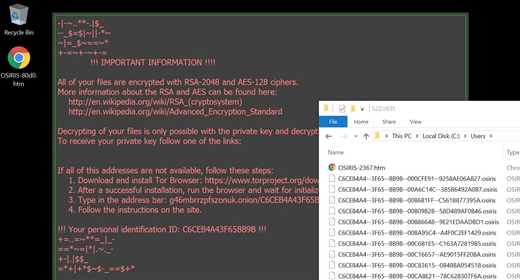
de_crypt_readme.html ransom notes edition
According to the reverse engineering analysis of obtained samples, this ransomware family is categorized as CryptXXX. At this point, the CryptXXX 2.0 edition of this Trojan is in the wild compromising Windows PCs. One of its distinguishing features is the use of the Angler exploit kit for distribution. This way, the extortionists have been depositing their infection onto computers by dint of hacked sites. The targeted web pages tend to be popular media-related portals for the most part, which means that a lot of users are at risk. When a person visits one of these covertly compromised places online, they get redirected to Angler EK’s landing page. The exploit kit then triggers a vulnerability check, finds security flaws in outdated software and uses those to inject the ransomware.
Courtesy of Kaspersky Lab, the first iteration of CryptXXX got cracked and users were able to recover their data with a specially crafted solution. The 2.0 version, though, isn’t possible to decrypt in this fashion, the victims getting an error that says “Encrypted file size does not equal to original”. Obviously, the black hats took the previous imperfections of their code into account and rolled out an update that keeps the decrypter from being efficient.
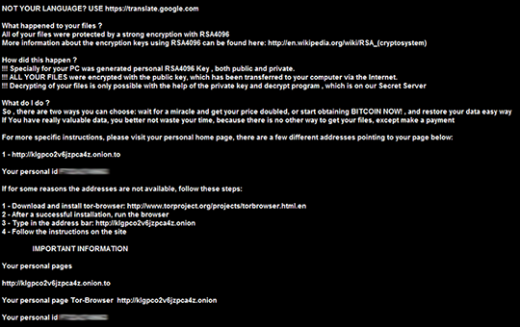
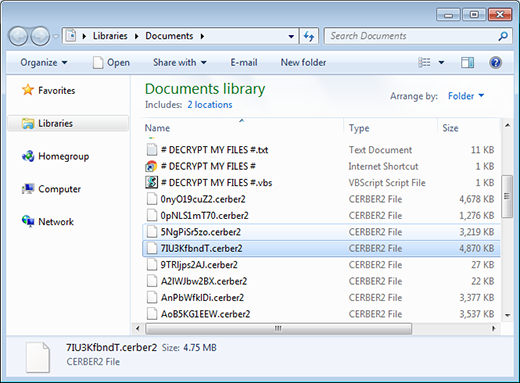
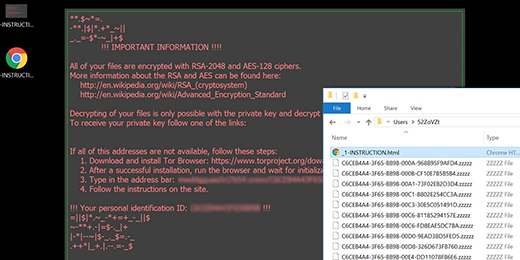
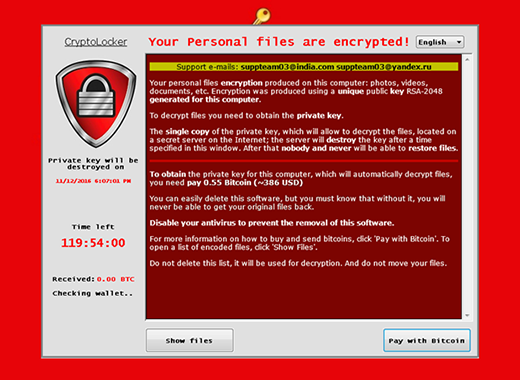
de_crypt_readme.bmp instructions added by .crypt file virus
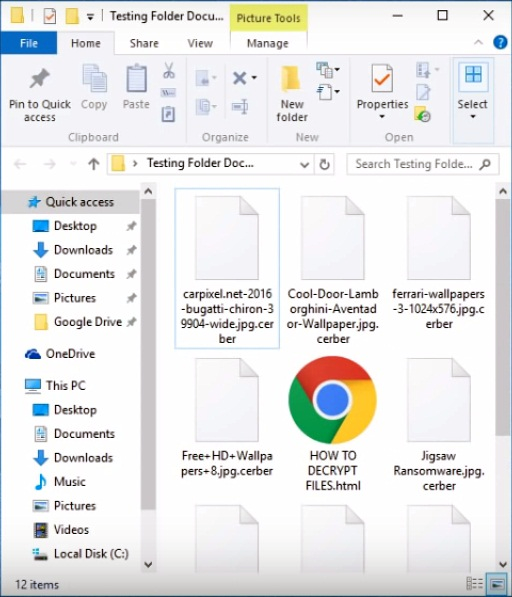
As it has been mentioned, the files hit by this Trojan get the .crypt extension at the end. Just to demonstrate this, here’s an example: an image chamomile.jpg turns into chamomile.jpg.crypt. It’s a no go to edit the filename by eliminating the .crypt part – the file will stay just as inaccessible as before. In order to determine what data objects to encode, CryptXXX scans the host machine’s hard drive, removable drives and mapped network shares for a predefined range of formats. It looks for potentially most important items, including one’s pictures, text documents, spreadsheets, presentations, databases and hundreds of other entities.

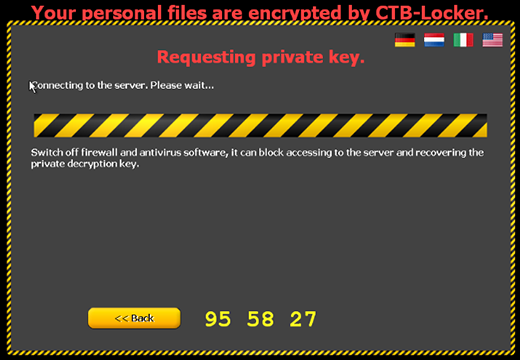
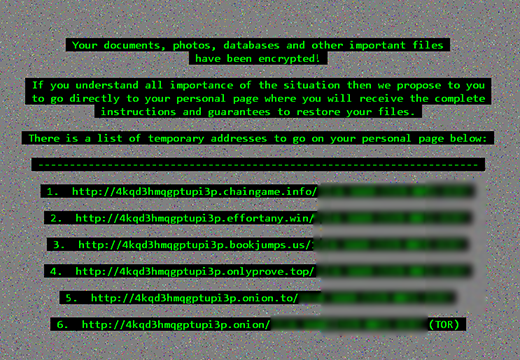
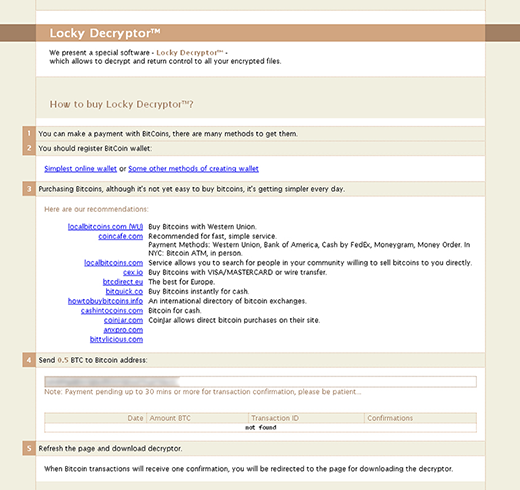
CryptXXX Decrypt Service page
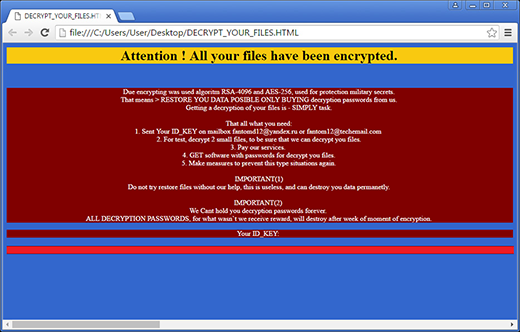
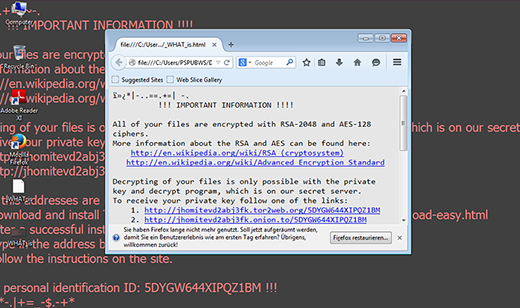
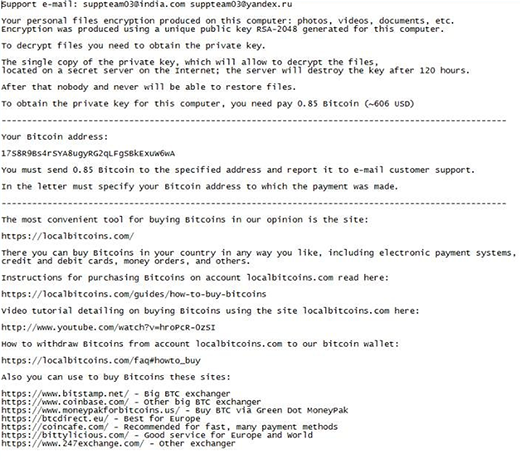
The above-mentioned de_crypt_readme.html (.bmp, .txt) ransom instructions tell the victim to purchase the private RSA4096 key in order to be able to decrypt the data. The price is set to 1.2 Bitcoins, or about 500 USD. This money is payable via a special Decrypt Service page protected by Tor (The Onion Router) anonymity network. The site displays a countdown clock indicating the amount of time left before the ransom doubles, and provides built-in payment options. Interestingly, the criminals call their recovery tool the “Google Decrypter”, which is evidently a lame attempt to add some trust to the attack.
All in all, the .crypt file extension ransomware assault is a bad turn of events. There is no decrypt software currently available, and submitting the ransom is an abominable thing. In a lot of the compromise incidents, however, users were reportedly able to retrieve their files using Shadow Explorer and professional recovery suites. So these techniques are certainly worth a try.
Automatic removal of .crypt virus
When it comes to handling infections like this one, using a reputable cleaning tool is the place to start. Sticking to this workflow ensures that every component of the ransomware gets found and eradicated from the affected computer.
1. Download and install the cleaning tool and click the Start Computer Scan button
Download .crypt files virus removal tool
2. The wait is worth it. Once the scan completes, you will see a report listing all malicious or potentially unwanted objects detected on your PC. Go ahead and click the Fix Threats option in order to get the ransom trojan automatically uninstalled from your machine. The following steps are intended to restore the encrypted files.
Recover .crypt files ciphered by the ransomware
Removing the infection proper is only a part of the fix, because the seized personal information will stay encrypted regardless. Review and try the methods below to get a chance of restoring the files.
Option 1: Backups
The cloud works wonders when it comes to troubleshooting in the framework of ransomware assault. If you have been keeping data backups in a remote place, just use the respective feature accommodated by your backup provider to reinstate all encrypted items.
Option 2: Recovery tools
The research of CryptXXX virus reveals an important fact about the way it processes the victim’s data: it deletes the original files, and it’s actually their copies that are encrypted. In the meanwhile, it is common knowledge that anything erased from a computer doesn’t completely vanish and can be dragged out of memory via certain techniques. Recovery applications are capable of doing this, so this method is surely worth a try.
Option 3: Shadow Copies
The Windows operating system incorporates a technology referred to as the Volume Snapshot Service, or VSS, which performs files or volumes backup routine automatically. One critical prerequisite in this regard is to have the System Restore feature toggled on. In case it has been active, some data segments can be successfully recovered.
You may perform this activity with the Previous Versions functionality, which is built into the OS, or by means of special applications that will do the job automatically.
- Previous Versions feature
Right-click on a file and choose Properties in the context menu. Find a tab named Previous Versions and click on it to view the last automatic backup that was made. Depending on a preferred action, click Restore to get the file recovered to its original location, or click Copy and indicate a new directory.![Previous Versions feature]()
- Shadow Explorer applet
It’s remarkably easy to manage Previous Versions of files and folders with automated tools like Shadow Explorer. This program is free to use. Download and install it, let it come up with a profile of the file hierarchy on the computer, and get down to the restoration proper. You can select a drive name on the list, then right-click on the files or folders to recover, and click Export to proceed.![Shadow Explorer]()
Did the problem go away? Check and see
Computer threats like ransomware may be stealthier than you can imagine, skillfully obfuscating their components inside a compromised computer to evade removal. Therefore, by running an additional security scan you will dot the i’s and cross the t’s in terms of the cleanup.
Download .crypt file virus scanner and remover
The post .crypt file extension virus: decrypt and remove de_crypt_readme ransomware appeared first on Keone Software.


![!Recovery_[victim ID].html ransom instructions !Recovery_[victim ID].html ransom instructions](http://keonesoftware.com/wp-content/uploads/de_crypt_readme-html.png)


![The '_[random number]_HELP_instructions.bmp' image becomes the desktop background The '_[random number]_HELP_instructions.bmp' image becomes the desktop background](http://keonesoftware.com/wp-content/uploads/zepto-desktop-background-520x265.png)