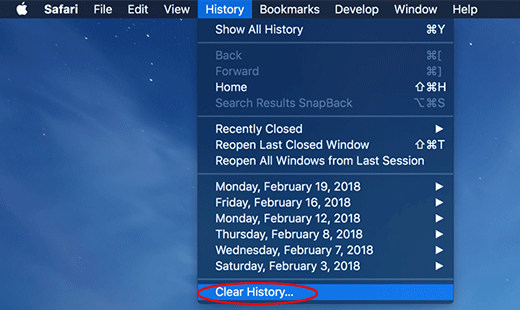
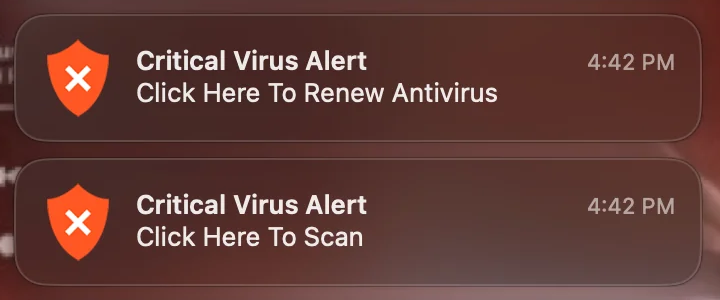
What’s particularly irritating about the Bing redirect virus is that it keeps the affected Mac users from searching the web with any other provider.
What is the Bing redirect Mac virus?
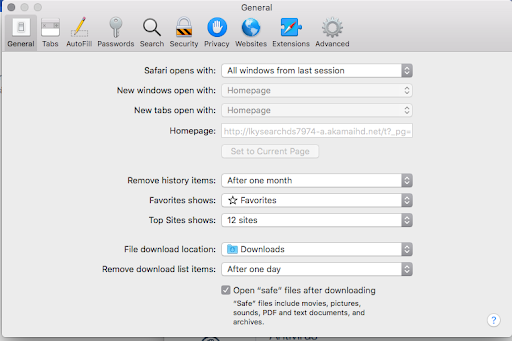
In today’s world of ubiquitous digitalization and high-end technologies, Internet traffic is a valuable product that costs money to obtain. Ideally, the end users maintain full control of which sites they visit and when. This paradigm drives permanent improvements of web services whose proprietors strive to offer something better than the others and thus entice people to get aboard. This is the ideal, ethical model that doesn’t always work the way it should, though. The Bing redirect Mac virus is an example of a crooked online marketing that definitely deviates from the norm. The Mac users who fall victim to this infection experience iterative Safari redirects to bing.com for seemingly no apparent reason.

Infected Mac users’ traffic is constantly forwarded to bing.com
It’s important to emphasize at this point that the landing page is an entirely legitimate search engine brought to millions of users by Microsoft, and blaming the twisted traffic on this provider is a misinterpretation. No wonder many victims find it strange that a piece of malware reroutes their Safari browser to the reputable, although far from the most popular search engine. There is an explanation to this oddity. Every single time the redirect happens, the Mac user’s online traffic is tunneled through several transitional domains. One of the interim URLs currently in rotation is searchbaron.com, with the sites switching from time to time. This activity is hardly visible to the naked eye, but technically, the intercepted web navigation follows a complex path and hits a number of web pages related to ad networks or similar services. In the end, it’s the trusted Bing homepage, so some infected Mac users go ahead and try to take a dive into the Safari settings to select the preferred provider. However, their efforts fail. Why? Because the configuration changes ensue from malicious activity.
The Bing redirect virus infiltrates Mac computers via a prosaic, yet effective technique. It’s about bundling, a method used to spread harmful applications alongside safe ones. These downloads are typically hosted on unofficial sources with poor reputation, where the individuals in charge rake in profits by cross-promoting various controversial programs. If the person who’s installing some nice little applet opts for the recommended (default) setup, they run the risk of additionally agreeing to install the malware without realizing it. Upon contaminating a Mac in such a furtive fashion, the infection gives Safari settings an overhaul and may also tamper with the system’s DNS settings.
As a result, whenever the victim tries to find random information via their search engine of choice, they will be ending up on bing.com in the long run. It’s due to this in-depth interference that the repair is more complicated than merely altering the browser settings by hand. Thankfully, there is a way to tackle the problem in a few minutes. Keep reading to get an idea of the Bing redirect Mac virus removal done right.
Automatic removal of Bing redirect virus from Mac
When it comes to handling infections like this one, using a reputable cleaning tool is the place to start. Sticking to this workflow ensures that every component of the virus gets found and eradicated from the affected Mac.
1. Download and install Combo Cleaner onto your Mac.
Download Bing redirect virus removal tool
2. Run the tool and click Start Combo Scan to have it check your Mac for threats. The wait is worth it. Once the scan completes, you will see a report listing all performance issues as well as malicious or potentially unwanted objects detected on your machine.

3. Go ahead and click the Remove Selected Items option in order to get Bing redirect virus automatically uninstalled from your Mac.
This being done, you should be good to go. Just to make sure everything went smooth, though, consider going through the steps below. Furthermore, be advised that Safari will still be redirected to bing.com until you rectify its settings (the reset procedure will be described further down).
Bing redirect virus manual removal from Mac
The gist of this section is to walk you through the process of deleting all non-obfuscated files related to the Bing redirect virus Mac. It’s best to perform the cleanup in the order specified below.
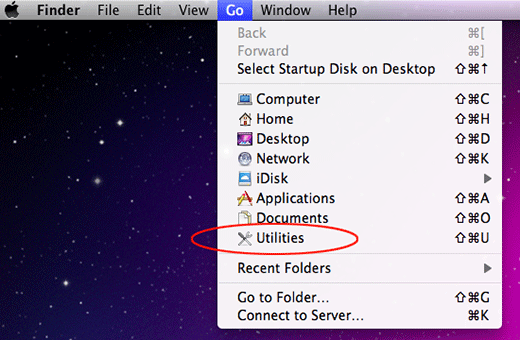
- Click the Go icon in Finder and select Utilities on the list
![Go to Utilities on Mac Go to Utilities on Mac]()
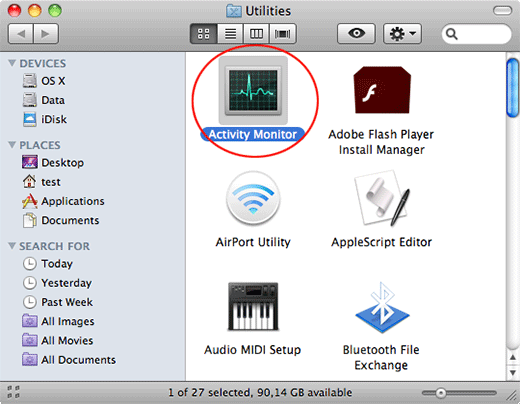
- Find and select the Activity Monitor under Utilities
![Access the Activity Monitor Access the Activity Monitor]()
- In the Activity Monitor, scrutinize the running processes for one that consumes lots of CPU and looks suspicious. Once the likely baddie is found, select it and click the Quit Process icon. An additional confirmation dialog will pop up – click Force Quit on it
![End the potential pest’s process End the potential pest’s process]()
- Now, go to Applications under the Go menu
![Go to Applications Go to Applications]()
- What you need to do is scroll down the list of installed apps in search of the malicious item. It could be a program with a gibberish name or one that ended up on your Mac beyond your awareness
![Uninstall the malicious app Uninstall the malicious app]()
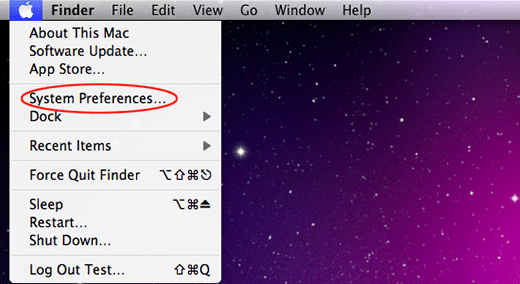
- Go to System Preferences as shown below
![System Preferences on Mac System Preferences on Mac]()
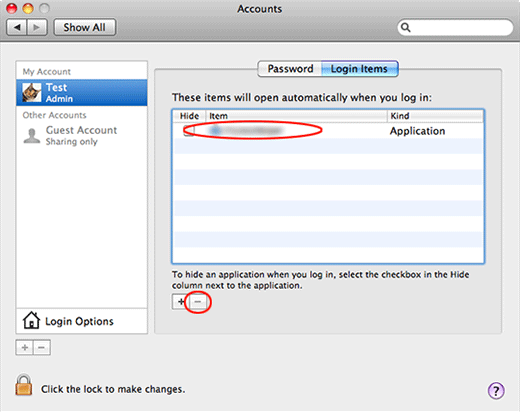
- Select Accounts, then Login Items. You will see all the apps that run as part of the Mac startup process. Find the infection and remove it from the list by means of the “minus” icon
![Minus out the malware from Login Items Minus out the malware from Login Items]()
Now that you have suppressed the virus proper, you need to fix the redirect problem in Safari. The browser defaults continue to be set to Bing, therefore the repair requires some manual configuration tweaking.
Remove Bing redirect Mac virus from Safari
The optimal troubleshooting method boils down to resetting Safari, which will undo all changes made by the infection or any third-party plugin without your permission. Here’s how to do it:
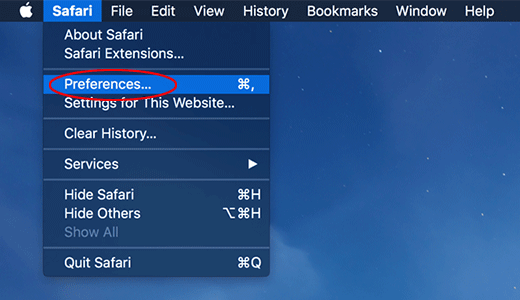
- In Safari, select Preferences as illustrated below
![Safari Preferences]()
- Go to the Privacy subsection and click the button saying Remove All Website Data
![Safari – Remove All Website Data Safari – Remove All Website Data]()
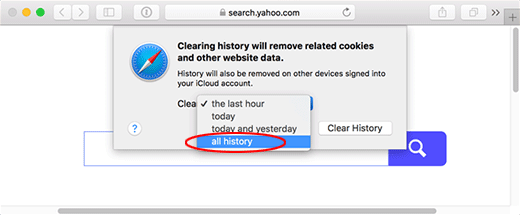
- The system will generate a popup message highlighting some must-know aspects of the refresh. For instance, the procedure will most likely log you out of sites you have accounts with. If that’s fine with you, click Remove Now on the dialog
![Website data removal in Safari – the confirmation Website data removal in Safari – the confirmation]()
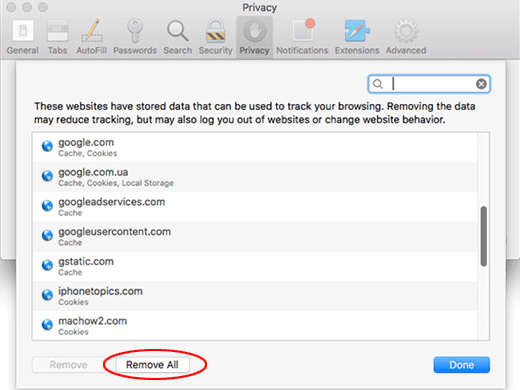
- You will now see a full list of websites that retain cache, cookies, and other data associated with your browsing sessions. One of the options is to pick the clearly dubious ones and click Remove. However, it’s recommended to select Remove All for a greater efficiency of the repair
![Remove fingerprintable data stored by websites Remove fingerprintable data stored by websites]()
- Hit the Done button to start fresh with Safari. The Bing redirect Mac virus is now completely removed and it won’t be meddling with your web surfing anymore.
The post Get rid of Bing redirect virus from Safari on Mac (MacBook Air/Pro, iMac) appeared first on Keone Software.